Industrial cybersecurity advice from ARC Advisory Group, Cybersecurity and infrastructure Security Agency (CISA) and the Idaho National Lab Cybercore Integration Center aimed to help attendees of the 2024 ARC Industry Leadership Forum.
Learning Objectives
- Review key industrial cybersecurity advice from 2024 ARC Industry Forum.
- Explore industrial cybersecurity threats, including recent ransomware increases and cyberattack examples provided by CISA.
- Understand ways Idaho National Lab cybersecurity can help with cyber-informed engineering.
ARC Industry Forum industrial cybersecurity insights
- Industrial cybersecurity advice was presented at the 2024 ARC Industry Forum.
- CISA offers help for recognizing industrial cybersecurity threats, avoiding ransomware increases and improving cyberattack resiliency.
- Idaho National Lab can help with cyber-informed engineering.
Industrial cybersecurity risks, strategies and responses were a significant part of the ARC Advisory Group’s ARC Industry Leadership Forum 2024, “Accelerate Transformation in the Age of AI, Cybersecurity and Sustainability,” Feb. 4 through Feb. 8. Experts from ARC Advisory Group, Cybersecurity and infrastructure Security Agency (CISA) and the Idaho National Lab Cybercore Integration Center provided advice to conference attendees. Speakers noted repeatedly the importance of training as part of an organization’s layers of defenses: One click from one employee may cripple an organization, its supply chain, customers and beyond, causing millions of dollars in damages.
Industrial cybersecurity: Today and tomorrow
Sid Snitkin, ARC Advisory Group vice president cybersecurity, said cybersecurity has never been more challenging than today and offered advice based on ARC research and collaboration (Figure 1). He’s participated in 12 years of cybersecurity discussions at the ARC Industry Forum. Snitkin said:

-
Ransomware and political unrest are increasing risks of operational disruption and safety incidents.
-
New regulations are amplifying compliance requirements.
-
Digitalization efforts are creating new kinds of cyber risks.
-
Challenges include cyber risk management, cybersecurity program management and cybersecurity solutions and services requirements.
-
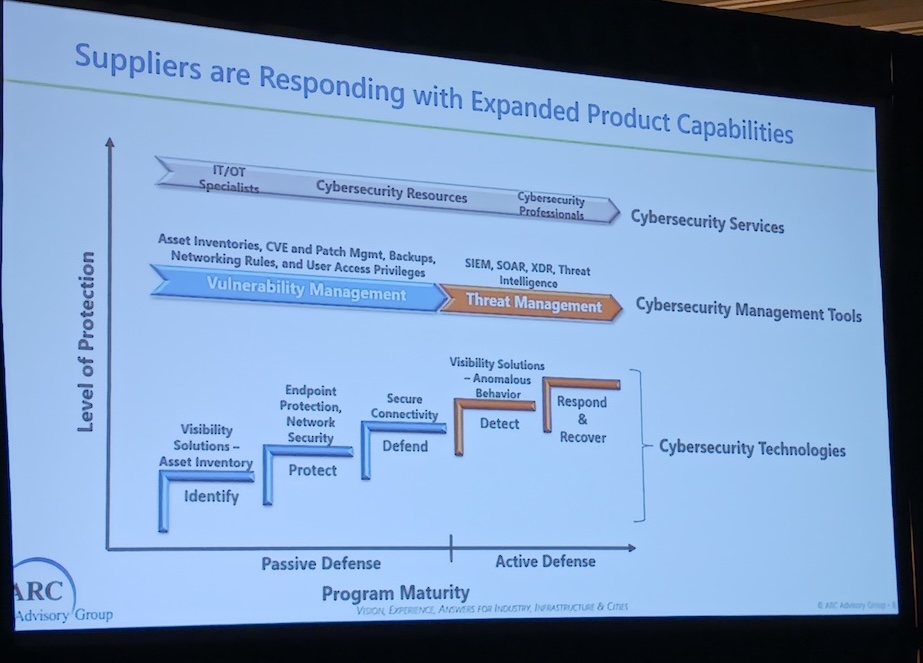
Backups often are an afterthought, but vendors are improving industrial cybersecurity tools, technologies and services (Figure 2).

A fall 2023 ARC report on cybersecurity, Snitkin said, looks at people, processes and technologies, covering cybersecurity services, management tools and technologies. Automation companies are taking a stronger role, including acquisition of cybersecurity companies. Rockwell Automation acquired Verve. Honeywell acquired ScadaFence. IT networking companies are enhancing OT functionality. Cybersecurity services providers are hiring more OT experts. Remote access requires special functionality.
Three steps to cyber resilient industrial operations, Snitkin said, are to:
-
Minimize likelihood of internal system compromises,
-
Minimize impact of internal compromises that still occur and
-
Minimize risk of compromised dependencies.
Ransomware expansion, more CISA experts to help
Jason Burt, regional cybersecurity adviser, Region IV, Cybersecurity and infrastructure Security Agency (CISA) explained how CISA helps protect the interdependent U.S. infrastructure (Figure 3). Threats to one are threats to all, he said. The U.S. federal government organization began in 2018 as the umbrella cyber-defense agency, providing resources, information, tools, training and gauging risks. Programs include interoperable telecommunications for first responders, security for elections and a cybersecurity adviser program across the 10 regions defined by the Federal Emergency Management Agency (FEMA). CISA has more than doubled expertise since 2022 and offers help starting at https://cisa.gov (Figure 4).

Burt said, “Across 16 infrastructure sectors, CISA works to help identify and verify, understand incidents, build and maintain tools, share information and collaborate. Only in chemical industry have we been given authority; we advise in other areas.” The organization also works with Federal Bureau of Investigation (FBI, which handles ransomware threats because data is held hostage, a federal offense), National Security Agency (NSA) and Secret Service.

Industrial cybersecurity threats, examples
Cybersecurity threats include terrorism, cyberattacks, extreme weather, pandemics, accidents or technical failures, Burt said, and noted that hurricanes bring more cyberattacks as enemies try to take advantage of system stress.
Ransomware efforts have increased with greater sophistication now at 5 to 10 per week in the
Southeast region that includes Florida, Burt said. Cyberattack concerns include sophisticated phishing, industrial internet of things (IoT) malware and vulnerability, data theft, fraud breaches, supply chain attacks, teleworking vulnerabilities, lack of protection/policies and advanced persistent threats (APTs), along with ransomware, insider threats (also unintentional threats from untrained employees), data breach for theft of personal identifiable information (PII) and intellectual property (IP) and denial of service attacks.
Examples of cybersecurity breaches in the last three years include:
-
Norsk Hydro (Norwegian Aluminum and Energy), $3.6 million paid by insurance to restore was only 6% of total cost; no ransom paid.
-
Airbus had a breach that used Turkish Airlines employee credentials to steal information via an employee’s home computer; 3,200 company documents were exposed.
-
Johnson Controls International and subsidiaries (Yokr, Tyco, Luxaire, Coleman, Ruskin, Grinnel and Simplex), Dark Angles Ransomware, $51 million ransom demanded, 27TB stolen data
-
BianLian Ransomware group had double extortion ransom attempts in January 2023 when 1.7TB was stolen from a California-based hospital.
Threats extend beyond the immediate company involved to supply chain threats, software service providers and outside contractors (often smaller, less secure companies with access to or credentials for larger organizations), mergers and acquisitions (inheriting lack of security), physical components (with exposure from hidden backdoors), network services and IoT (when prioritizing time-to-market is more valued than cybersecurity.)
Cybersecurity compromises via software providers
Cybersecurity breaches also can originate from “trusted” sources.
-
NotPetya: June 2017, M.E.Doc Tax Software Update caused more than $10 billion in damages globally. Origin was Russia targeting Ukraine, which has been a Russian hacker digital playground, Burt said. Wiperware progressed from from system to system, erasing information. “What happens if you update tax software and download malware. This spread internationally to many who did business with Ukraine. Spread included ATMs, point of sales and transportation.
-
SolarWinds Orion IT Monitoring Software, February 2020, caused $30 million in damages to public and private organizations; backdoor malware was delivered via an update to thousands of companies in U.S.
-
Kaseya – VSA Product, July 2021, had 800 to 1500 victims and more than $70 million in damages, ransomware, Miami; managed service providers were infected through a server-based update.
Advanced threats, Burt said, include social engineering, scattered spider, SIM swapping, account takeovers and data exfiltration.
CISA advice to counter industrial cybersecurity threats
Artificial intelligence and machine learning (AI/ML) neural networks, large language models and generative AI may help against some cybersecurity threats, Burt said, but also are being used by hackers.
Know that all companies are at risk; don’t think that good operational technology (OT) cybersecurity is enough, Burt warned. Ways to lower cybersecurity risk include to:
-
Train employees; one email can shut down an enterprise and connected suppliers and customers.
-
Enable multifactor identification, but avoid text-based authentication because texts can be intercepted, but it’s better than nothing, Burt said.
-
Use strong password phrases, such as J0hnny eAts piZza 0utSide..!
-
Don’t open links in unknown email and look carefully at email for spoofs.
-
Follow new cybersecurity guidance and regulations to avoid fines for non-compliance and increased management liabilities. U.S. rules are changing to require near-immediate reporting of cybersecurity incidents, but information reported will not be available for litigation or Freedom of Information Act requests.
-
Don’t pull the power cable which can deleted need forensic information, but do disconnect from networks.
-
Scrutinize potential larger attack surfaces from IoT devices, cloud and edge devices and software and connected workers.
-
Only use backups known to not be affected. Because hackers often are in the system for 30 days or longer, restoration copies may need to reach back that long or longer.
-
Use CISA services, regional and national resources, tools and best-practice assessments. If nothing else, use CISA cyber-hygiene scanning of your organization’s outward-facing footprint, which is what threat actors see. Anyone who subscribes can opt-out anytime.
Idaho National Lab cybersecurity help, cyber-informed engineering
Sam Chanoski, Idaho National Lab, technical relationship manager, Cybercore Integration Center, offers technical leadership, expertise and strategic insights and works with Department of Energy (DoE), Department of Homeland Security (DHS) and Department of Defense (DoD) on various projects (Figure 5). He works on how to use engineering to influence cybersecurity in a positive way, like industry did for safety.

Cybersecurity changes happen more quickly than the lifecycle for most industrial software, devices and systems, Chanoski suggested, so it’s important to plan for resilience. During a cyber crisis, interdependencies inside and beyond an organization are exposed. Organizations need to realize and understand consequences of cyberattacks and may need to make a leap of logic to understand how digital systems could work in unintended ways. To simplify, organizations need to assume what’s possible. Appropriate planning for a cyberattack may mean the difference between a catastrophic day and a bad day.
Industrial safety can be compared to cybersecurity in some ways, Chanoski said. Safety metrics are measured by the presence of defenses, not by the absence of incidences. Cybersecurity can be similarly confident with the presence of effective defenses, in layers, independent and redundant. Those who don’t know where to start should begin a discussion to begin to adopt a cybersecurity philosophy and mindset. Not everything can be protected but an organization can devote a higher level of resources to assure the most critical function or functions, Chanoski said. Managing digital assets (devices, systems and networks) is needed. Just one lost computer, in the wrong hands, can harm an organization (and has), Chanoski said.
Consider cybersecurity as risk management. INL is working on about 100 pages of system lifecycle questions to ask. “Look them over and let us know what we forgot. We’re working on version 2,” Chanoski said. To learn more about how to manage cyber risk from concept to operation, INL’s Cyber-Informed Engineering (CIE) effort, go to https://Inl.gov/cie.
Chanoski said that cybersecurity culture is the sum of individual behaviors and influenced by organizational choices. “I’m not sure we’ll ever do it ‘right.’”
Mark T. Hoske is content manager, Control Engineering, CFE Media and Technology, [email protected].
KEYWORDS: Industrial cybersecurity, cybersecurity advice
CONSIDER THIS
What happens when your industrial cybersecurity is tested with one back click?
ONLINE
https://www.arcweb.com/industry-concepts/cybersecurity-maturity-model