Organizations can use timely and actionable operational technology (OT) cybersecurity insights to help identify and respond to the latest threats.
Learning Objectives
- Understand the importance of operational technology (OT) cybersecurity insights
- Understand the different types of cybersecurity insights along with the capabilities they can provide users.
- Learn how to implement insights into the overall cybersecurity posture.
OT cybersecurity insights
- In response to escalating cyber threats, organizations are prioritizing cybersecurity insights, crucial for defending against potential attacks, enhancing operational resilience and threat prevention.
- Cybersecurity professionals face challenges in the industrial sector, including a shortage of OT-specific skills.
- Tailored software solutions that provide site-level and enterprise insights are vital for organizations to assess, manage risk, and ensure compliance in the evolving OT environment.
In the wake of high-profile ransomware attacks disrupting gasoline distribution at Colonial Pipeline and meat production at JBS Foods, many organizations have increased their focus on building more comprehensive cybersecurity programs to improve their ability to protect their operational technology (OT) assets. One of the key capabilities in defending against growing threats is by developing advanced and actionable cybersecurity insights.
What cybersecurity insights do
Cybersecurity insights are similar to early warning radar for an air force trying to defend its airspace. A country trying to defend its airspace is blind without detection abilities and contextual insights into what could be attacking it.
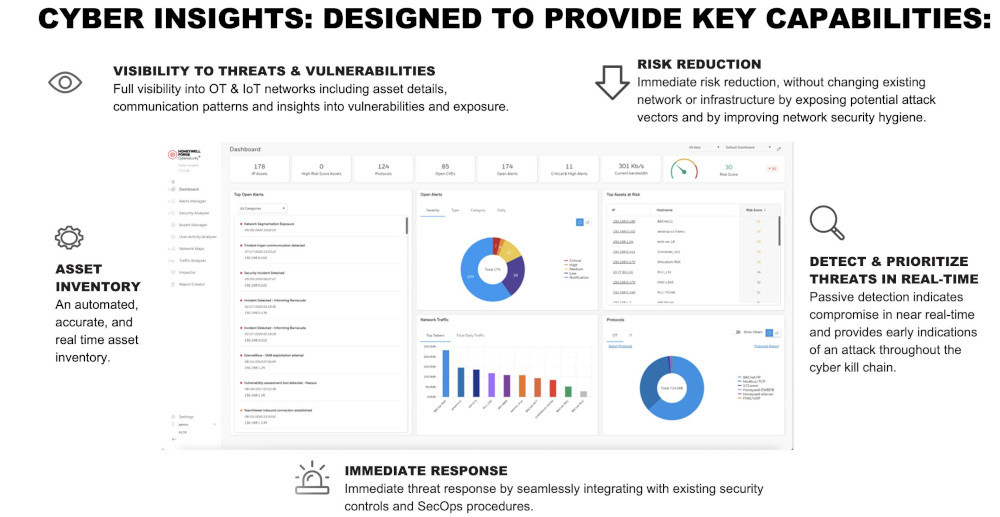
Insights go deeper than simple threat detection. They provide critical analysis of cybersecurity threats and actionable data into how to best address the intrusion. By combining detection with context, insights can provide cybersecurity managers with a critical understanding about potential intrusions. Organizations can then use these insights to decide on how to respond. This could include distinct actions depending on characteristics of the threat. They might include new firewall rules, system quarantine and/or bringing assets offline to install patches as countermeasures to address a particular intrusion.
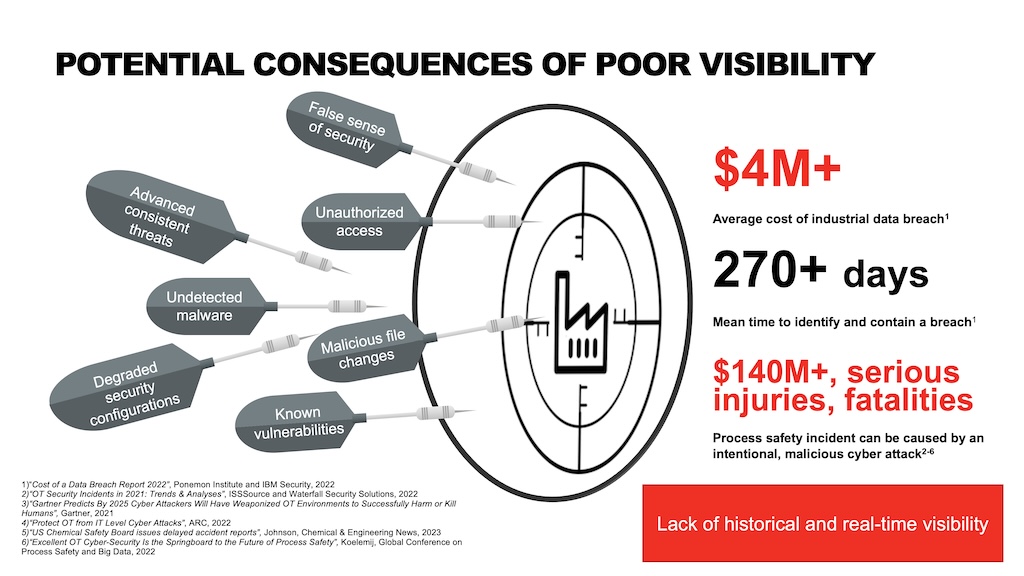
Quite a few organizations have threat detection capabilities, but many lack OT-specific contextual insights, which leave them vulnerable to threats. Insights can bring vital information to help determine the scope and severity of intrusion. They can also better inform decision making on how to respond to threats. These insights must be able to provide the organization with near real-time data about identified threats and vulnerabilities.
The importance of cybersecurity insights in today’s OT environment
Hackers are becoming more sophisticated, particularly with cyber-physical attacks, by refining intrusions from generic designs to specific targets. They also continue to introduce new tactics and techniques and improve upon their capabilities to manipulate industrial protocols.
Increased sophistication and new intrusion methods are not the only concerns. The industrial sector faces a sustained risk and higher volumes of malware infiltrating and disrupting operations. Even worse, an increasing volume of malware can establish control of operational assets.
According to the 2023 USB Threat Report, some of the key findings included:
-
More than 53% of all detected malware are designed to penetrate industrial systems via a USB and establish command and control (C2), which is an increase from 9% in 2019.
-
Malware capable of disrupting crucial industrial operations, is up to 82% from only 26% in 2019.
Without clear insights into cyber-physical threats, the potential for disruption increases. For example, cybercriminals can use malware to gain access into industrial systems, establish remote control and install malicious payloads.
Insights can provide cybersecurity managers with a better understanding of threats and their characteristics so they may be able to prevent some of these serious risks to their operations.
Types of cybersecurity Insights
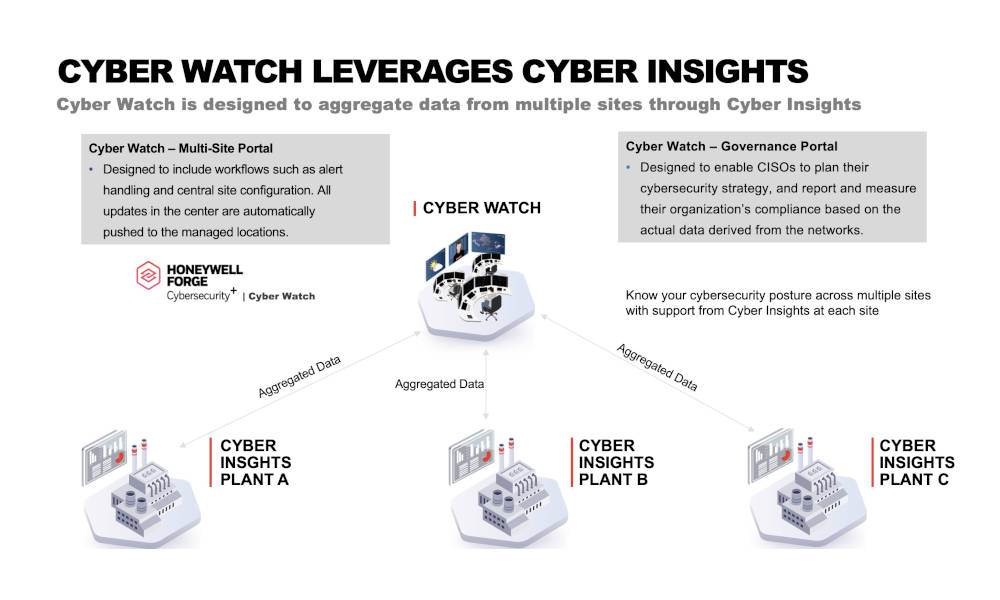
All cybersecurity insights are not the same. There are two distinct types organizations may use in their cybersecurity management. Cybersecurity vendors offer software solutions providing site-level and enterprise insights.
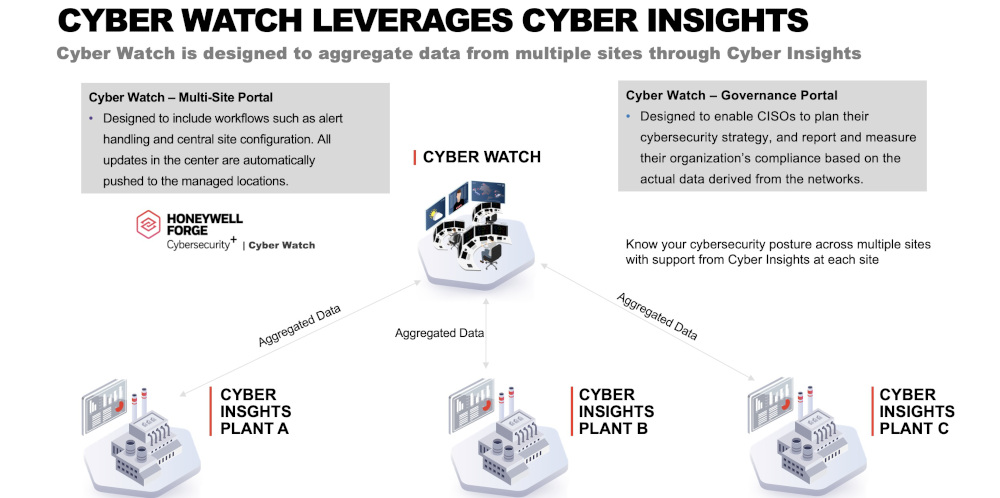
Site-level insights include data on vulnerabilities, threats and compliance issues detected at an individual site. These site insights can be used by cybersecurity managers located on site or at headquarters to better understand cyber security threats so they can isolate and neutralize them.
Enterprise insights are slightly different. In addition to offering a view of site-level data and threats, they include a portfolio-wide view of anomalous behavior and threats. A chief cybersecurity officer, CISO or senior corporate leader often has access to enterprise insights. They can help cybersecurity leaders understand OT risks by providing visibility through enterprise dashboards using near real-time data across all sites.
Both types of insights bring their own levels of visibility and value. Many large companies will need both types of insights. An organization with one or two locations might only need site-level insights. However, since insights are a key enabler to respond to threats, organizations should determine which types fit best with their organizational structure to quickly respond to cybersecurity risks.
Improved cyber experience and compliance
Cybersecurity service providers offer customized software solutions to help organizations with threat detection and visibility. They also can help organizations to meet challenges related to the scarcity of in-house OT cybersecurity experience and improve an organization’s ability to achieve critical compliance outcomes.
There continues to be a shortage of cybersecurity professionals with skills in operational technology. According to a study by ISC2, there is a cybersecurity workforce gap of more than 3.4 million people.
Insights are more critical than ever because OT risk visibility and response may be limited in organizations where OT risks are not fully understood. Companies also may have a portfolio of OT assets that are very complex.
Risk compliance is as critical in OT as in the information technology (IT) space. Cybersecurity managers must stay compliant with regulations and standards that apply to distinct assets and operating environments. A software solution can also help organizations in meeting and recording important compliance requirements. This capability becomes even more important in an OT environment that generates a growing volume of security data.
Building insights into a cybersecurity program
All organizations need to first assess the cybersecurity posture of their OT assets and risks. This includes evaluating their systems, networks, policies, procedures and OT assets. An OT cybersecurity professional can conduct a cybersecurity assessment designed to map out OT assets, analyze their functions, document their network connections, examine risks associated with the connected assets, and classify identified vulnerabilities by severity. The assessment is also designed to help examine how effective the existing security procedures and controls are in responding to cyber threats.
Once the assessment is complete, organizations can use the assessment findings to help them begin to understand insight gaps in how they understand risk. Leaders may decide insights are not sufficient to provide adequate detection and response to OT cyber risks. At this point they should consider cybersecurity vendors who offer software solutions capable of providing better insights for responding to OT risks at both the site and enterprise-level.
These insights can help an organization address these vulnerabilities and help the organization to improve availability, reliability and safety of their industrial control systems and operations.
For organizations that need an enterprise-wide solution, some vendors offer software solutions that enable insights across multiple sites. They should choose a solution that provides needed visibility and actionable insights to better understand threats and act against them.
Developing effective cybersecurity insights
Building OT cybersecurity resilience requires having timely and actionable insights. A complex operating environment with a vast inventory of OT assets, growing connectivity, OT skill shortages and more sophisticated cyber threats make insights more important than ever in improving security for an organization’s operations.
Organizations must develop insights that can help them achieve better visibility into their cybersecurity posture so they can quickly respond to identified OT threats in their operations.
Implementing cybersecurity insights helps companies improve their ability to identify and mitigate incidents across their enterprise. These insights can help an organization prevent incidents that cause significant threats to companies’ production, safety and reputation.
Nav Sharma is senior cybersecurity product management lead at Honeywell. Edited by Chris Vavra, web content manager, CFE Media and Technology, [email protected].
MORE ANSWERS
Keywords: Cybersecurity, operational technology (OT)
CONSIDER THIS
What cybersecurity insights do you consider most important?
REFERENCES
Newsweek, “Gas Shortages, Long Lines Across Southeast After Colonial Pipeline Cyberattack,” Khaleda Rahman, May 11, 2021. https://www.newsweek.com/gas-shortages-long-lines-after-colonial-pipeline-cyberattack-1590345
Wall Street Journal, “Ransomware Attack Roiled Meat Giant JBS, Then Spilled Over to Farmers and Restaurants.” Jacob Bunge and Jesse Newman, June 11, 2021. https://www.wsj.com/articles/ransomware-attack-roiled-meat-giant-jbs-then-spilled-over-to-farmers-and-restaurants-11623403800
Honeywell USB Threat Report. October 2023.
https://hcenews.honeywell.com/CYB-WEB-EN-GLOBAL-Q3-2023-Threat-Report-LP.html
ISC2 2022 Cybersecurity Workforce Study. https://www.isc2.org/Research/Workforce-Study#